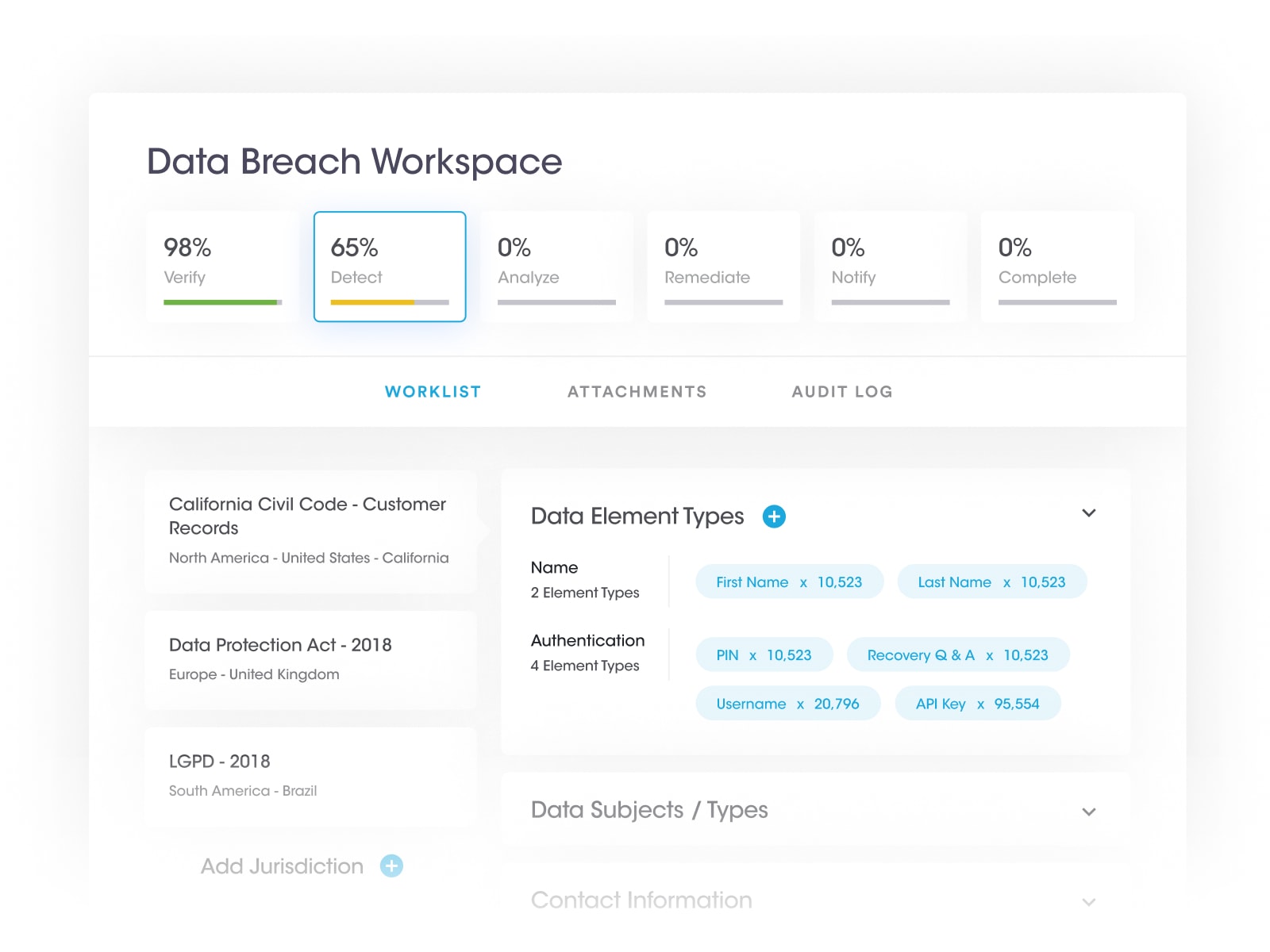
how to log a data breach
Confirm the breach has happened but be cautious of emails Find out. Computing devices containing personal data being lost or stolen.
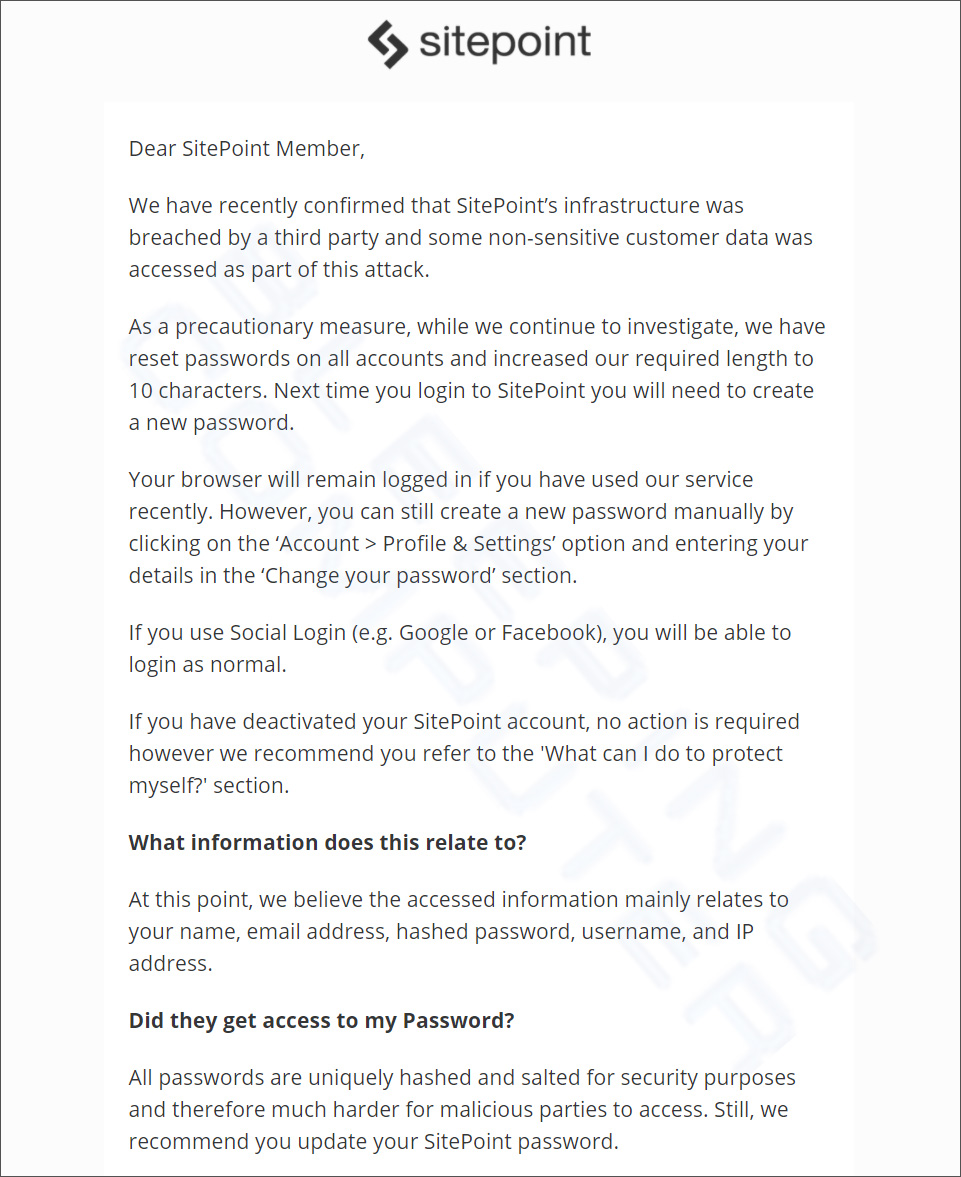
Sitepoint Discloses Data Breach After Stolen Info Used In Attacks
Data breaches can happen anywhere and its important to know what to do if you are affected by a data breach.

. Definitions of Breach Terms. The first step of the investigation of data breach is to determine the. Sending personal data to an incorrect recipient.
As a data controller you have created I presume what would colloquially be called a data breach log consisting of breaches of the DPA involving you as a data controller. Subsequently have frameworks set up to help distinguish and contain breaks. The quicker a Data breach can be identified and dealt with the lower the expense.
A data breach happens when someone accesses a network and views or copies an organizations data without authorization. An email data breach can happen when there are security issues with an email. A data breach occurs when cybercriminals steal information from an organizations database without permission from the owner or administrator.
The log should describe the. Implement tools services and policies. A data breach is any unintentional release of secure or private data.
This can include classified information belonging to the military sensitive information relating to. Meaning cybercriminals can gain access to your information through an organisation website. Data breaches are extremely.
Heres What To Do After a Data Breach 7-Steps Watch on. We will instantly notify you if we. Identify the Data Breach.
If your Social Security number or financial information was part of a data breach freezing your credit will restrict access to it which makes it challenging for. Most companies in the US are required to notify customers of breaches. To prepare for a data breach event policies actions and tools can be put in place to lay out a plan for detecting and containing an.
Before we continue discussing. Wait for an email. Deliberate or accidental action or inaction by a controller or processor.
We will continuously monitor your personal and financial information for any potential threats on the dark web and beyond. According to the GDPR legislation an organization must report a data breach to a data protection authority DPA also known as a supervisory. Instructions to Report A Data.
Your first priority at this point in time is to isolate the affected system s to prevent. Cyber insurance can also help companies before an event takes place by helping supply the companies with. GDPR requires all firms to keep a log of any and all breaches even the smallest incidents should be recorded.
Freeze Your Credit. Submit a Notice for a. Follow These 8 Steps After a Data Breach.
According to Trend Micro a data breach is an incident where information is stolen or taken from a system without the knowledge or authorisation of the systems owner. Heres a look at some of the most common types of data. Cyberciminals target businesses or government.
Dont wipe and re-install your systems yet Do follow your incident response plan. The covered entity must submit the notice electronically by clicking on the link below and completing all of the required fields of the breach notification form. Types Of Data Breach.
However there are 7 phases that you should follow for data security breaches. Data breaches are a reality and its something that businesses need to be prepared for. Here are the top five ways to find out if a site you use has been breached.
Data Breach Incident Log Template. When to report a data breach under GDPR. Technically a data breach is a violation of security protocol for an organization or individual in which confidential information is copied transmitted viewed and stolen by an.
The only thing worse than a data breach is multiple data breaches.
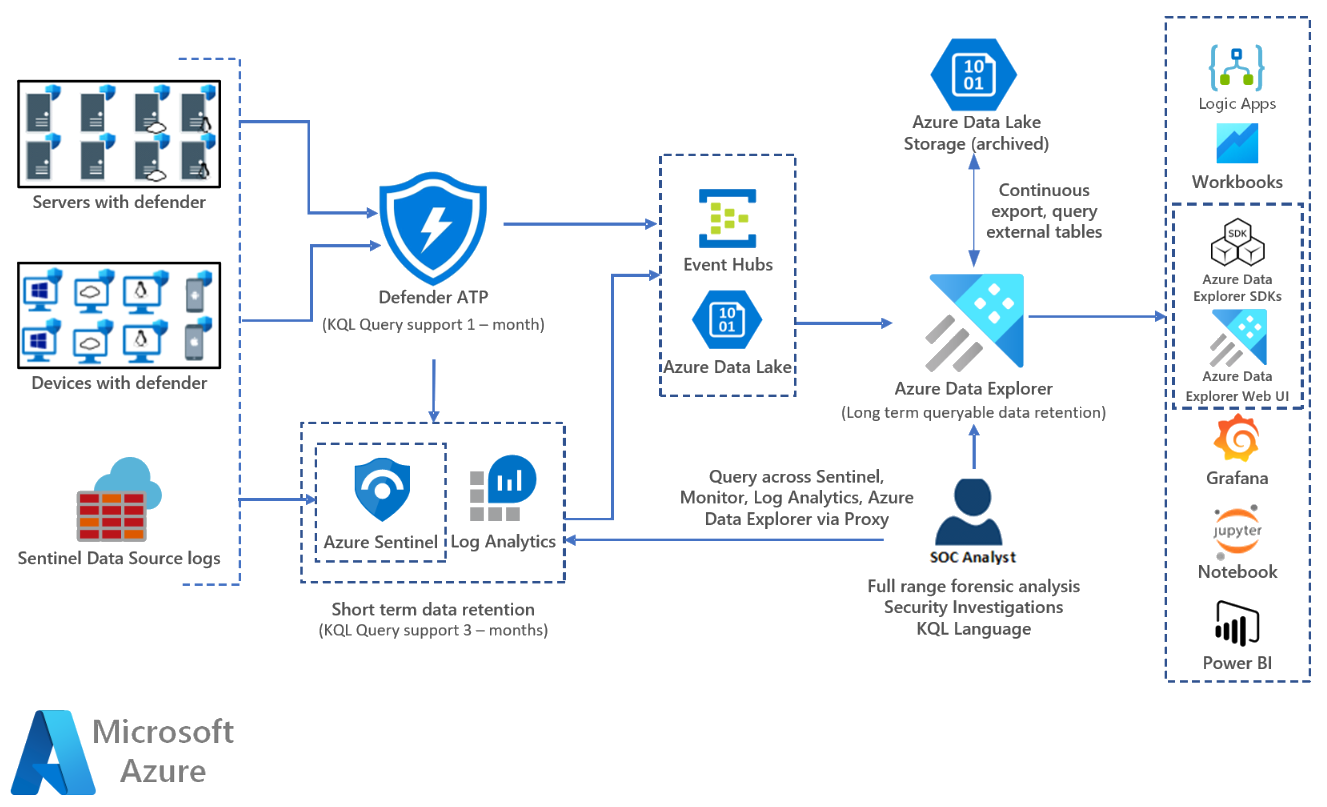
Long Term Security Log Retention With Azure Data Explorer Azure Architecture Center Microsoft Learn

Timeline Of The World S Biggest Data Breaches

Data Breach Register Gdpr Templates

Data Breaches Guidance For Individuals And Families Ncsc Gov Uk

What Should You Do After Data Breach Data Breach Insights

What Is A Data Breach Definition Types Dnsstuff

The Importance Of Account Protection And Incident Response Plans

What To Do After A Data Breach The Mozilla Blog

Personal Data Breaches Support And Information Zone

Here S What You Should Do After A Data Breach Experian
Cathay Pacific Suffers Data Breach Affecting 9 4 Million Customers
What Is A Data Breach Definition And Related Faqs Cyral

5 Real Life Data Breaches Caused By Insider Threats Ekran System
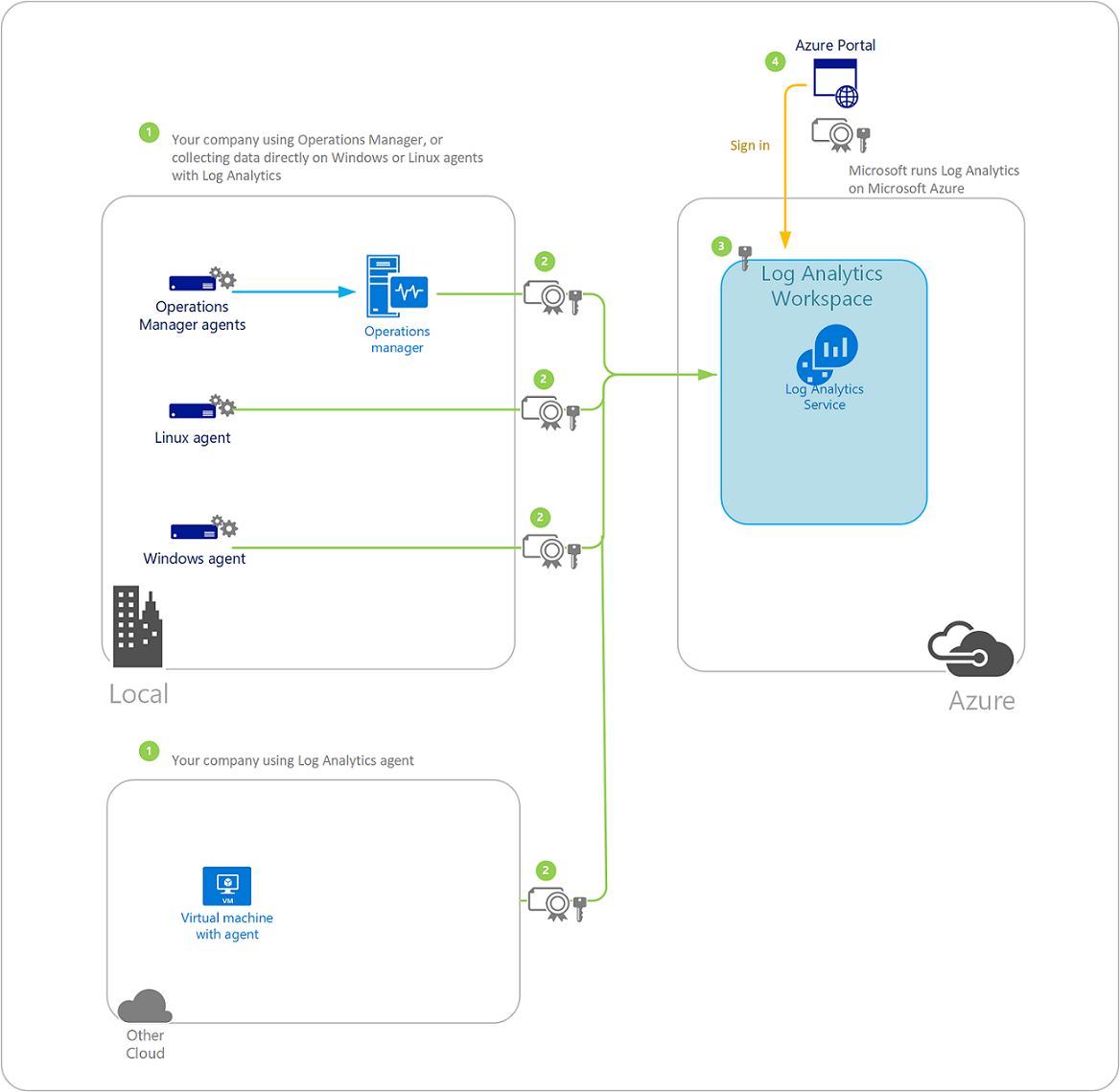
Azure Monitor Logs Data Security Azure Monitor Microsoft Learn

Gdpr Data Breach Register Are You Looking For This Gdpr Data Breach Register In Ms Excel Implementing A Data Breach Register Is C Data Breach Data Templates

The Likelihood Of A Data Breach Within An Organisation Payments Cards Mobile